Zscaler Data Breach: Attackers Compromise Salesforce Environment
A new cyberattack has put the spotlight on one of the biggest names in cloud security, Zscaler. Recently, attackers broke into its Salesforce environment, raising serious concerns about how safe our data really is in the cloud. Salesforce is widely used across industries to store customer and business information. When a system like this is compromised through a data breach, the impact is not small. It becomes a reminder that even companies built to protect us from threats can also become victims.
We live in a time where businesses depend heavily on cloud and SaaS platforms. They give us speed, scale, and flexibility. But at the same time, they create new entry points for hackers. The Zscaler breach is not just about one company. It is a wake-up call for all of us to rethink how secure our digital environments really are. Let’s find out what happened, why it matters, and what lessons we can learn to protect our own systems.
About Zscaler
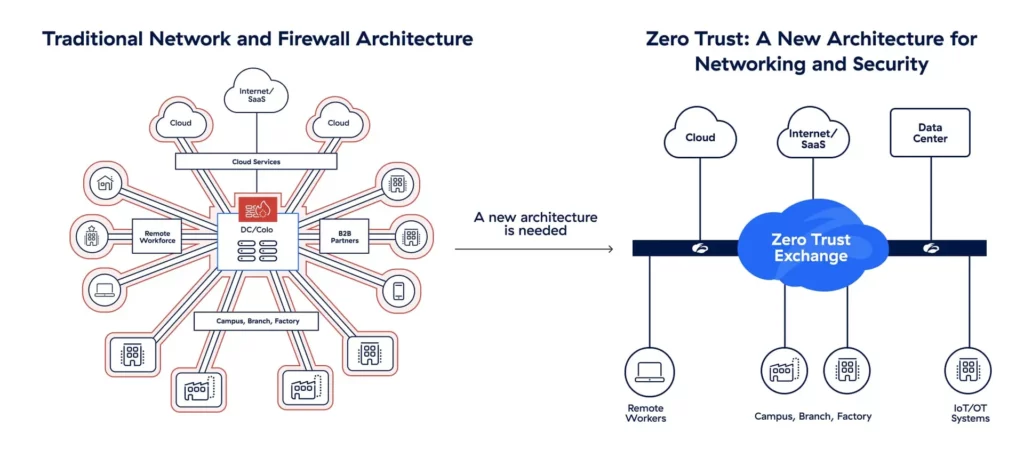
Zscaler is a major cloud security company. Its services protect traffic and enforce zero-trust policies for large firms. Many enterprises rely on Zscaler to filter threats and secure remote work. The company also publishes research on threats and cloud risk. Its role makes any breach especially worrying. Zscaler’s teams move quickly when incidents occur. The company said the issue was limited to its Salesforce instance and did not touch its core products or infrastructure.
The Zscaler Data Breach Explained
Attackers gained access through a third-party integration tied to Salesloft Drift. Threat actors stole OAuth tokens that let the third-party app talk to Salesforce. Those tokens provided limited access to some Salesforce records. Zscaler reported that support case contents and customer contact details may have been visible. The company revoked the app’s access and rotated API tokens. Zscaler also tightened customer authentication for support calls and launched a vendor risk review. The firm emphasized that its production systems and internal infrastructure were not breached.
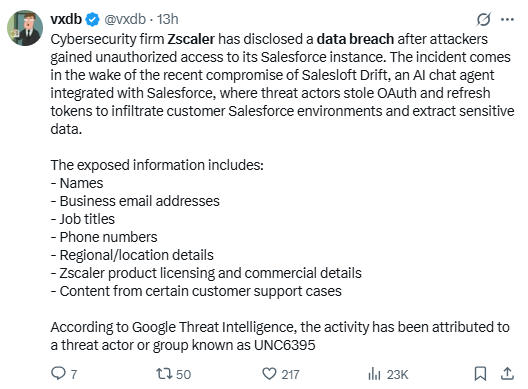
Timeline matters. The Salesloft Drift campaign affected many Salesforce customers in mid-2025. Security researchers traced the campaign to coordinated attempts that abused OAuth and connected apps. Victims included high-profile brands across sectors, and attackers used similar techniques to bypass multi-factor protections by exploiting granted OAuth scopes. In Zscaler’s case, the company disclosed the incident publicly after confirming the limited scope and taking containment steps.
Salesforce as an Attack Vector
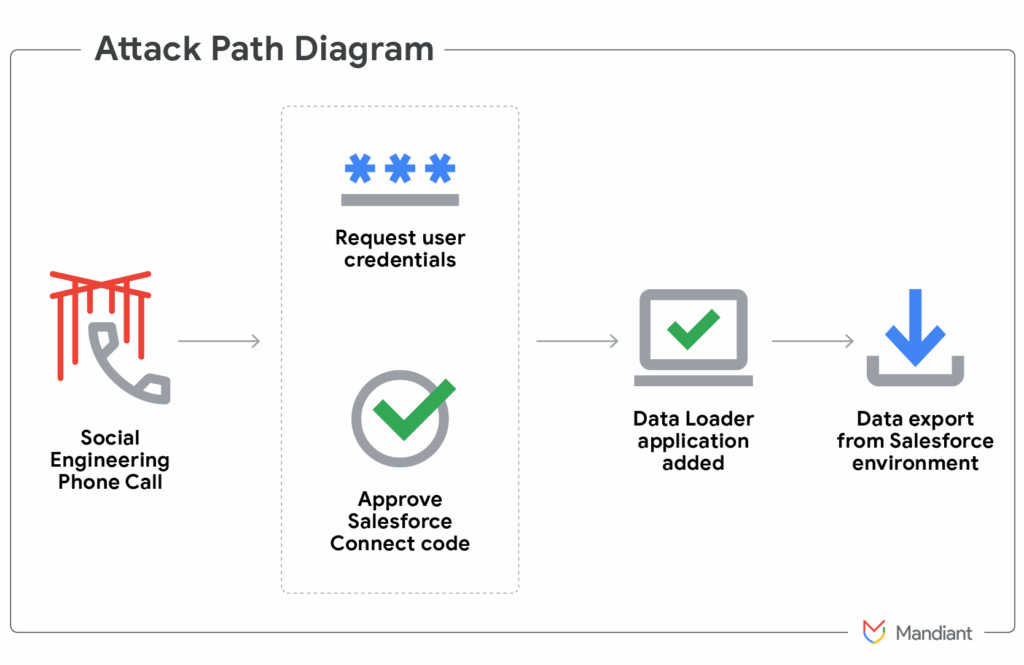
Salesforce stores vast amounts of business and customer data. It also connects to many third-party tools. Those integrations make it a rich target. OAuth tokens and connected apps can grant wide permissions. If those tokens are stolen, attackers can query data via APIs. Social engineering, supply-chain abuse, and fraudulent connected apps have been proven ways to get such access. That pattern helps explain why attackers keep returning to Salesforce ecosystems. Security teams must treat SaaS integrations as crown jewels, not mere conveniences.
Impact on Zscaler and Customers
For Zscaler, reputation risk is the main concern. The firm defends other companies from breaches. News of a data exposure undermines trust. Customers will ask hard questions about vendor controls. Regulators may also seek details depending on what personal or regulated data was exposed.
For affected customers, the immediate risks include phishing and targeted scams. Stolen support-case information can give attackers context. That context can help craft convincing social-engineering attempts. Zscaler’s quick steps to revoke access and force token rotation aim to limit further harm.
Industry Reactions & Expert Opinions
Security analysts say this incident is part of a wider trend. Experts warn that SaaS-to-SaaS links are often weak points. Many recommend strict controls on third-party apps and routine audits of OAuth scopes. Some researchers pointed to the Salesloft Drift compromise as an enabling event that allowed attackers to pivot into many Salesforce customers’ environments. Vendors and security teams now face pressure to harden supply-chain and identity protections across SaaS ecosystems. Public statements from Zscaler and others stress rapid mitigation and deeper vendor reviews.
Broader Trend: Cloud & SaaS Security Risks
Recent months saw multiple attacks on Salesforce instances and related tools. Attackers use similar playbooks: target a third party, steal credentials or tokens, then extract CRM data. The scale of some incidents shows how a single vendor compromise can ripple across many organizations. This reality challenges the traditional perimeter model. It also shows that zero-trust ideas must extend to vendor relationships and SaaS apps. Companies must map their dependencies and assume attackers can use trusted integrations against them.
Preventive Measures & Best Practices
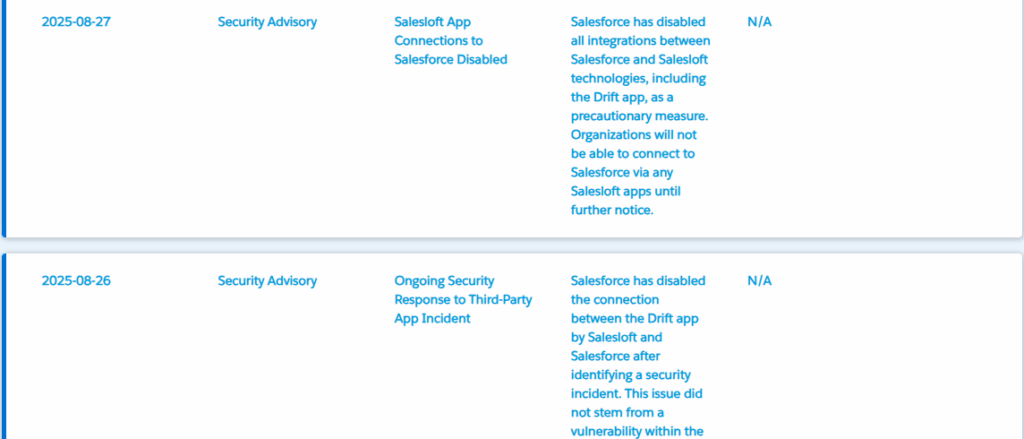
Limit plugin permissions. Grant third-party apps the minimum scopes they need. Revoke unused connected apps promptly. Enforce short token lifetimes and rotate credentials regularly. Require app vetting and contractual security clauses for vendors. Use least-privilege access controls in Salesforce and log all API activity. Enable anomaly detection on API calls and set alerts for large exports. Strengthen customer support authentication to prevent social-engineering attacks that aim to change or reveal sensitive data.
Finally, run tabletop exercises that include supply-chain compromise scenarios. Salesforce and security experts also recommend centralized visibility for all SaaS connections and periodic audits of OAuth permissions.
Wrap Up
The Zscaler incident shows how complex modern security has become. A trusted vendor can be the avenue for exposure. The breach underscores the need for tighter SaaS hygiene and stronger third-party risk programs. Moving forward, organizations should treat integrations as sensitive assets. That change requires strong identity controls, continuous monitoring, and clear vendor governance. The goal is simple: reduce the blast radius when a linked service is breached.
Frequently Asked Questions (FAQs)
On August 28, 2025, Zscaler confirmed it exposed only limited Salesforce support case data and customer contact details. The company said attackers did not access core infrastructure, production systems, or sensitive financial records.
Attackers used stolen OAuth tokens from a third-party integration linked to Salesforce. These tokens gave them limited access to records, which Zscaler quickly revoked to prevent deeper damage.
Disclaimer:
This is for informational purposes only and does not constitute financial advice. Always do your research.






